Yesterday we talked about how to create and use a One Time Pad. Today we will talk about another way of encoding messages. I am sure I am not creating anything new with this method, but I have not seen it before nor do I have a name for it. My working name is Word Grid Substitution.
Description of the Method
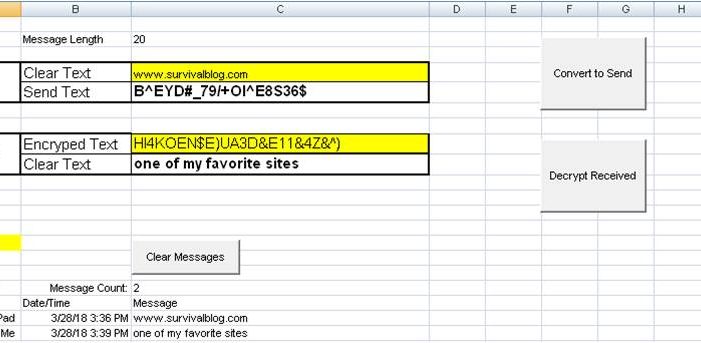
The heart of this method is a 25,000 word grid. The current word grid is 10×2500. I take the message to be encoded and search for the first word from a random spot in the list. When the word is found, the coordinates are then recorded. The encoded message is then a simple list of grid coordinates. Your contact would need to have the exact word grid and spreadsheet to decode the message.
Building the Word Grid
I used a lot of public sources to gather this list of words for the word grid. I pulled in several open source books. Then, there was some work to do word frequency counts to help determine two things– determine what words appear frequently in the English language and in what ratio they appeared. For example, the word “the” appears in the word grid 63 times, the letter “a” 28 times, the letter “I” 30 times, and the word “one” five times. This allows the messages to contain the same words but show different encodings, so that word patterns are harder to spot. I also used word lists on different topics as well as a lot of abbreviations, acronyms, country names, capitals, states, books of the Bible, body parts, food names, plants, trees, et cetera.
Numbers Converted to Words
The list contains no actual numbers, only the words for numbers. I wrote a specific macro that converts numbers into words. The reason for this is that I would need every number included within the word grid, otherwise. By converting to words, I just need the number words along with words like hundred, thousand, million, et cetera. For example: 1,234.56 would be converted to “one thousand two hundred thirty four point five six”.
New Words
I still find new words that I do not have in the grid from time to time. When this happens, the user is prompted to substitute a similar word and then continue to encode. The missing word is then added to a list. The next time the word grid is updated, that word will be included.
Sorting The Word Grid
I sort the word grid by using the same approach as yesterday’s example. I sort the first column only, then sort the first two columns using column two as the key. Then I sort the first three columns using column 3 as the key. I follow that pattern all the way to the end using all ten columns and using the tenth column as the key. This leaves column ten in alphanumeric order. I solve that by then using Excel’s random number generator to number each of the rows, and sort the entire grid by that column.
I also use this same process to sort through the rows. This ensures that words are moving between rows and columns during the sorting process.
Using With Multiple Contacts
I wanted to be able to use this spreadsheet with multiple contacts. I had the idea of using simple offsets to accomplish it. By this I mean that when the message is encoded the grid coordinates are offset with a predetermined offset number. For example, if the word “one” had a coordinate of 844-3 and I had an agreed upon offset with Group Bravo to use an offset of +10,-1, the coordinate would become 854-2. This would allow for somewhat secure communications with several groups that might share this same spreadsheet. If the message was meant for all groups, there would be no offset.
Challenge and Response to Authenticate
When using open communication sources, such as radio, I would also suggest using some form of a challenge and response system to authenticate that you are talking with your correct contact. An exchange might go like this:
- BaseStationA – “Alpha calling Bravo” – spoken English
- BaseStationB – “This is Bravo, go ahead” – spoken English
- BaseStationA – Issues the Challenge Code Tango 6 encoded as “854-9 802-1”
- BaseStationB – Responds with encoded response Zulu 3 encoded as “1287-4 1350-2”
- Each station then crosses off their challenge and response from their list and continues their encoded conversation
This would basically be a challenge and response list that both you and your contact have. After one has been used, it is crossed out and the next one is used for the next conversation.
How To Use
This method of encoding will really rely on the use of a computer to encode and decode the message. The large word grid that is needed really takes away the ability for this to be portable. However, with a much smaller word grid and predetermined communication protocols, it might still be possible. It just wasn’t my intention when I created this.
Like yesterday’s encoding method, you could send the encoded messages over the Internet with a separate computer via text message or email, via radio (with no coded messages over Ham radio until the SHTF), dead drop, Morse code, et cetera.
Pros & Cons
Pros
- Faster transmission using numbers
- Easier typing
- Built-in spell checker (so that it finds the exact word in the word grid)
- Message history by group name
Cons
- Not portable with a 25,000 word grid
- Still possible to detect word patterns even with high volume words in the word grid multiple times
- Takes a lot of work to create the word list
Security For Whatever Method You Choose
Like a lot of the choices that we make for being prepared, you will need to decide what level of security you will need for your method of communications. We have to determine what level or for what event(s) we are preparing our preps. Communication is no different.
Questions to Think About
There are some questions to think about. These include:
- Do you just want to be able to communicate with your next door neighbor down the road?
- Is your communication with a group a few miles away?
- Are you using a Ham radio to reach out across the state?
- Who could potentially hear you?
- How secure do you need to be to keep the wrong person, group, or agency from hearing your communications?
- Is the radio secure enough even with encoding the messages?
- Should dead drops be used?
- Do you have an air gapped computer available?
- How do we securely share updated OTPs within our group and community?
- Should I preprint OTPs now so that they are available if there is no electricity?
- Is your communication gear protected from a natural or man-made EMP?
There are many more questions to ask and a lot more ways to secure your communications depending on the importance of the message.
Refreshed and Updated Encoding
Do not forget to think about how often your source of encoding should be refreshed and updated. For example, should you update your OTP every month or just wait until you have used all of the pads? You might also think about having an emergency OTP available in case you feel you have been compromised. Also think about what method you use to share the updated OTP data with your group and others. Flash drives could contain viruses. Again, there are many things to think about.
Final Thoughts
I have seen a lot of discussion in articles promoting certain email services and phone apps talking about their end-to-end encryption methods. That is all well and good, but I would like to control my own encryption. I do not want to rely on someone else’s program or service to control my security. Who knows if these programs might have back doors in them?
How Often We Should Encrypt
There is also some discussion from security experts about how often we should encrypt our email, messages, and overall communications. What seems to be the suggestion from many of them is that we should do two things– encrypt everything that we can, and everyone should encrypt. Both of these opinions stem from the same idea. If you personally only encrypt your very important messages, then that is a sign to whoever might be looking or listening that that message is very important. That makes sense. Likewise, if you are the only one encrypting and most of the people in your sphere of influence are not, then that might highlight your activity more than theirs.
If everyone encrypts everything then it becomes more difficult to determine which messages are important and which people should be watched more closely.
Practice…Before SHTF
And finally, practice whatever method(s) you choose to use. A SHTF event is not the time to learn new things.
See Also:
SurvivalBlog Writing Contest
This has been part one of a two part entry for Round 76 of the SurvivalBlog non-fiction writing contest. The nearly $11,000 worth of prizes for this round include:
First Prize:
- A $3000 gift certificate towards a Sol-Ark Solar Generator from Veteran owned Portable Solar LLC. The only EMP Hardened Solar Generator System available to the public.
- A Gunsite Academy Three Day Course Certificate. This can be used for any one, two, or three day course (a $1,095 value),
- A course certificate from onPoint Tactical for the prize winner’s choice of three-day civilian courses, excluding those restricted for military or government teams. Three day onPoint courses normally cost $795,
- DRD Tactical is providing a 5.56 NATO QD Billet upper. These have hammer forged, chrome-lined barrels and a hard case, to go with your own AR lower. It will allow any standard AR-type rifle to have a quick change barrel. This can be assembled in less than one minute without the use of any tools. It also provides a compact carry capability in a hard case or in 3-day pack (an $1,100 value),
- Two cases of Mountain House freeze-dried assorted entrees in #10 cans, courtesy of Ready Made Resources (a $350 value),
- A $250 gift certificate good for any product from Sunflower Ammo,
- Two cases of Meals, Ready to Eat (MREs), courtesy of CampingSurvival.com (a $180 value), and
- American Gunsmithing Institute (AGI) is providing a $300 certificate good towards any of their DVD training courses.
Second Prize:
- A Model 175 Series Solar Generator provided by Quantum Harvest LLC (a $439 value),
- A Glock form factor SIRT laser training pistol and a SIRT AR-15/M4 Laser Training Bolt, courtesy of Next Level Training, which have a combined retail value of $589,
- A gift certificate for any two or three-day class from Max Velocity Tactical (a $600 value),
- A transferable certificate for a two-day Ultimate Bug Out Course from Florida Firearms Training (a $400 value),
- A Three-Day Deluxe Emergency Kit from Emergency Essentials (a $190 value),
- A $200 gift certificate good towards any books published by PrepperPress.com,
- RepackBox is providing a $300 gift certificate to their site.
Third Prize:
- A Royal Berkey water filter, courtesy of Directive 21 (a $275 value),
- A large handmade clothes drying rack, a washboard, and a Homesteading for Beginners DVD, all courtesy of The Homestead Store, with a combined value of $206,
- Expanded sets of both washable feminine pads and liners, donated by Naturally Cozy (a $185 retail value),
- Two Super Survival Pack seed collections, a $150 value, courtesy of Seed for Security, LLC,
- Mayflower Trading is donating a $200 gift certificate for homesteading appliances, and
- Two 1,000-foot spools of full mil-spec U.S.-made 750 paracord (in-stock colors only) from www.TOUGHGRID.com (a $240 value).
Round 76 ends on May 31st, so get busy writing and e-mail us your entry. Remember that there is a 1,500-word minimum, and that articles on practical “how to” skills for survival have an advantage in the judging.










Another alternative for privacy is the book code. Two or more people have a copy of the identical book, and you use page numbers and word numbers to convey your message. Without knowing which book you are using, anyone who intercepts your messages only sees a series of numbers. An example: 122 32, 154 16, 12 136. Common books, like the New King James Version of the Bible, should be avoided. Likewise, JWR’s books should be avoided by regular readers of this website, since the association is too easy and those will be the first books chosen in an attempt to decode your messages. You can expand your selection by numbering (randomly, of course) a series of books. A warning, if you use a bookcase full of books, the user will be tempted to mark them with the book number which defeats the purpose if discovered.
The problem is that any coded message will attract attention. So if someone was looking for surreptitious activity this would be a red flag. Then you have people watching you.
An additional problem is that codes can be broken. The better the code and the more confident the code user is the more likely that serious secrets/information will be encoded and put at risk. This “could” lead to a complete reveal of everything that needs to be kept secret.
Also be advised, by FCC rules and regulations, it is illegal to send coded messages over any HAM / Shortwave / CB frequency(s). But… when (a real world) ‘Schumer Hits The Fan’ event happens and there is no longer any or very limited, rule of law, who’s gonna’ know?
My suggestion is to practice either by written message and send it via US Mail to your contact(s) and / or via email or text.
It’s fun doing it this way, it’s like solving a puzzle. Give it a try, you’ll like it!
My preference is to use encoding using relatively innocuous phrases, all based on a common theme (such as a weather report or a request for contact). Those phrases can be cross coded to the real meanings using a rotating or one-time pad of phrase sets.
For instance, the first phrase would identify the particular phrase set to be used:
“Weather looks cloudy with a chance of rain” – Means use phrase set Y (for instance)
“Our weather is predicted to be clear and sunny” – Means use phrase set X
“Please contact use at 3:00pm tomorrow” – Means use phrase set Z
Each phrase set should be based on a common theme, ie. weather, contact request, etc..
Needless to say, having a larger number of phrase sets and either rotate them for each use or designate each to be a one-time usage and agree to never use a set more than once.
The downside to this is that both parties need a copy of the phrase sets and a means to keep them secure. If one side is compromised, both sets become unusable…
The downside scenario can be addressed by an agreement which is NEVER written down, but is required to be memorized by both sides. For instance, the order of the “Next Phrase Set To Be Used” should be a memorized sequence. This is NOT totally secure because one side could be tortured to obtain the phrase sequence. TANSTAAFL
Book codes are by no means secure. Modern cryptanalysis programs have every book, in every edition and every language every published. So breaking a book code is relatively easy with modern computing powers.
One time pads are the only way to pass a secure message. Any computer program, while giving the appearance of randomness in creating numbers is a psydo-random, as it uses something to generate that number, usually the computer clock or some variance. If the computer has ever been connected to the internet then it has the potential to have been compromised.
The only way to create a completely OTP is to use 10-sided dice, usually a set of 5 to generate 5-number group. AmRRON dark labs have created a random number generator that is a stand alone device, and the code source is open so you can verify no false code is there.
The other rule for OTP is that is is only used once (unless you are using for training).
Having codes for words or phrases longer than a 5-digit group shortens the message.
I posted this in yesterday’s article, but since I don’t think it will be seen and answered there, I’ll ask it again here.
There were (valid) complaints against using MS Excel to create the secure message spreadsheet.
What about using Apache OpenOffice (any of the several variations)?
WOW!!! Dayton Prepper! This is extremely comprehensive. I think that this is really great for Base stations. I wonder how could you do this if on the Move? I guess it could be the Same. I am going to look at this more in depth with my “Networks” comm people. Maybe we can incorporate this for future comms.