Email a copy of 'Creating Your Own Secure Messages – Part 2, by DaytonPrepper1' to a friend
7 Comments
- Ad Seed for SecurityOur Colossal Survival Pack is now on sale for 25% off. This pack contains over 5 pounds of non-GMO, open-pollinated seeds packed for long term storage.
- Ad Civil Defense ManualThe Civil Defense Manual... The A to Z of Survival. Look what in it... https://civildefensemanual.com/whats-in-the-civil-defense-manual/

Another alternative for privacy is the book code. Two or more people have a copy of the identical book, and you use page numbers and word numbers to convey your message. Without knowing which book you are using, anyone who intercepts your messages only sees a series of numbers. An example: 122 32, 154 16, 12 136. Common books, like the New King James Version of the Bible, should be avoided. Likewise, JWR’s books should be avoided by regular readers of this website, since the association is too easy and those will be the first books chosen in an attempt to decode your messages. You can expand your selection by numbering (randomly, of course) a series of books. A warning, if you use a bookcase full of books, the user will be tempted to mark them with the book number which defeats the purpose if discovered.
The problem is that any coded message will attract attention. So if someone was looking for surreptitious activity this would be a red flag. Then you have people watching you.
An additional problem is that codes can be broken. The better the code and the more confident the code user is the more likely that serious secrets/information will be encoded and put at risk. This “could” lead to a complete reveal of everything that needs to be kept secret.
Also be advised, by FCC rules and regulations, it is illegal to send coded messages over any HAM / Shortwave / CB frequency(s). But… when (a real world) ‘Schumer Hits The Fan’ event happens and there is no longer any or very limited, rule of law, who’s gonna’ know?
My suggestion is to practice either by written message and send it via US Mail to your contact(s) and / or via email or text.
It’s fun doing it this way, it’s like solving a puzzle. Give it a try, you’ll like it!
My preference is to use encoding using relatively innocuous phrases, all based on a common theme (such as a weather report or a request for contact). Those phrases can be cross coded to the real meanings using a rotating or one-time pad of phrase sets.
For instance, the first phrase would identify the particular phrase set to be used:
“Weather looks cloudy with a chance of rain” – Means use phrase set Y (for instance)
“Our weather is predicted to be clear and sunny” – Means use phrase set X
“Please contact use at 3:00pm tomorrow” – Means use phrase set Z
Each phrase set should be based on a common theme, ie. weather, contact request, etc..
Needless to say, having a larger number of phrase sets and either rotate them for each use or designate each to be a one-time usage and agree to never use a set more than once.
The downside to this is that both parties need a copy of the phrase sets and a means to keep them secure. If one side is compromised, both sets become unusable…
The downside scenario can be addressed by an agreement which is NEVER written down, but is required to be memorized by both sides. For instance, the order of the “Next Phrase Set To Be Used” should be a memorized sequence. This is NOT totally secure because one side could be tortured to obtain the phrase sequence. TANSTAAFL
Book codes are by no means secure. Modern cryptanalysis programs have every book, in every edition and every language every published. So breaking a book code is relatively easy with modern computing powers.
One time pads are the only way to pass a secure message. Any computer program, while giving the appearance of randomness in creating numbers is a psydo-random, as it uses something to generate that number, usually the computer clock or some variance. If the computer has ever been connected to the internet then it has the potential to have been compromised.
The only way to create a completely OTP is to use 10-sided dice, usually a set of 5 to generate 5-number group. AmRRON dark labs have created a random number generator that is a stand alone device, and the code source is open so you can verify no false code is there.
The other rule for OTP is that is is only used once (unless you are using for training).
Having codes for words or phrases longer than a 5-digit group shortens the message.
I posted this in yesterday’s article, but since I don’t think it will be seen and answered there, I’ll ask it again here.
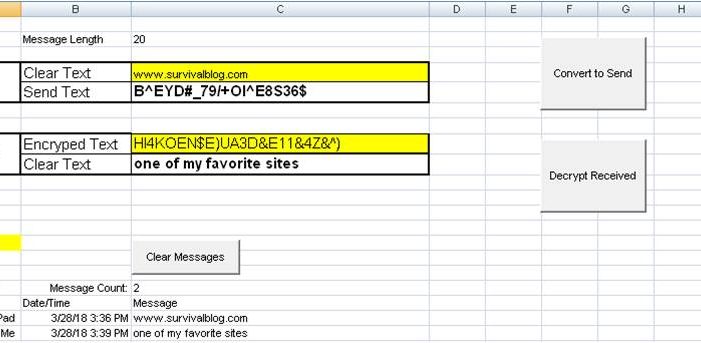
There were (valid) complaints against using MS Excel to create the secure message spreadsheet.
What about using Apache OpenOffice (any of the several variations)?
WOW!!! Dayton Prepper! This is extremely comprehensive. I think that this is really great for Base stations. I wonder how could you do this if on the Move? I guess it could be the Same. I am going to look at this more in depth with my “Networks” comm people. Maybe we can incorporate this for future comms.