What is it? We often hear the term OPSEC, also know as Operations Security (not Operational Security), but few people actually know what it really means. When asked they often say, “It means not talking about what you are doing.” Or, they may say, “It means staying gray.” This is an extremely simplistic view of the program and fails to incorporate the nuances and methodology of the process.
The concept is nothing new. In the fifth century BCE, Sun Tzu wrote, “If I am able to determine the enemy’s dispositions while at the same time I conceal my own, then I can concentrate and he must divide.” The idea of keeping military information closely held has been practiced by the U.S. military in every war and conflict.
Being that OPSEC is a military program, let’s look at the official definition:
“An analytical process used to deny an adversary critical information about our planning process and operations.”
That is all well and good, but what does that really mean and where did it come from? OPSEC, as a formalized security program, came from a Vietnam era NSA effort called “Purple Dragon”.
In 1965, LBJ ordered bombing missions against Viet Cong (VC) and North Vietnamese Army (NVA) targets in SE Asia. These missions operated under the code names ARC LIGHT and ROLLING THUNDER. By 1966 it was becoming obvious that the bombing missions were not having the desired effects. U.S. ground units and bomb damage assessments were showing there were far fewer VC and NVA personnel and equipment in the targeted areas that intelligence reports had predicted. After a year of heavy bombing and the expenditure of millions of dollars, ARC LIGHT and ROLLING THUNDER appeared to be a failure.
Why was our intelligence so faulty? There must be a reason. As U.S. intelligence dug deeper, they noticed an increase of CHICOM message traffic during these bombing missions. Somehow the Chinese, and thus the NVA, were aware of the U.S. missions before they were launched! These messages even contained extremely detailed target information and warned VC and NVA units up to eight hours in advance.
DoD established a team to investigate this situation. The investigation was codenamed PURPLE DRAGON. PURPLE DRAGON discovered several items of interest, but one stood out. Under International Civil Aviation Organization (CAO) rules, any time that an aircraft moved out of one Air Traffic Control (ATC) jurisdiction into another it was mandated that it file a flight plan with the local ATC and let the new ATC know when and where it would be entering the new ATC’s jurisdiction. The new ATC would release a Notice to Airmen (NOTAM) listing flight path, altitude, times of arrival, and other details of the specific aircraft’s itinerary. NOTAMs were available to all civil aviation authorities. This information was sent to all adjacent ATCs, so they would also be aware of the aircraft.
B-52 missions flying out of Guam and Thailand were required to file flight plans as required with the local ATC and thus to the world in the form of a NOTAM. North Vietnam was receiving these NOTAMs via the CAO and were able to extrapolate target data from the documents. This gave ample time to warn potential targeted units and locations with up to eight hours to vacate the area and make defensive preparations.
The Purple Dragon team were able to identify the vulnerability in this process. Using this example the team developed a process to review, analyze, and protect unclassified information that could be exploited by our enemies. They focused on indicators, patterns, and signatures of upcoming operations. This process became Operations Security or as we know it today: OPSEC.
The process is pretty straightforward in a military setting but not so clear in our private lives. We talk about not standing out but how do we accomplish this. What are we trying to protect, and who are our adversaries? Should these issues be addressed in our dealings on the Internet?
Let’s look at that definition again: “An analytical process used to deny an adversary critical information about our planning process and operations.”
It really is as simple as this:
- What information do you want to protect?
- Who wants your information?
- How is your information vulnerable?
- What is the risk for your information?
- How can you protect your information?
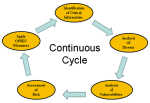
The OPSEC process consists of five steps. The text book answer is that they are not in any particular order, but personally I like the following:
- Analyze the Threat.
- Identify Critical Information
- Analyze Your Vulnerabilities.
- Assess the Risk.
- Apply OPSEC Countermeasures.
Analyze the Threat
Who are our enemies and what are they capable of? Are your enemies street criminals, identity theft scam artists, the Mafia, burglars, armed robbers, and/or terrorists? A person living in Atlanta would have a different set of threats (street criminals, et cetera) than a rancher in Arizona (drug runners from Mexico, et cetera). An owner of a logging company may be threatened by eco-terrorists, like Earth Liberation Front, where a butcher may be targeted by the Animal Liberation Front. Conduct research in your area, and determine what the local threats are to you! These may be drastically different than that of your neighbor or local friend.
When analyzing the threat, look at the group’s existence, capability, intent, history, and targeting.
Identify Critical Information
Put yourself in the mind of the adversary. As yourself, “If I were going to attack this person, what info would I need to execute the assault?” For our purposes, we will use an example of identify theft. I would want to know: name, SSN, DOB, account numbers, address, credit card numbers, POB, phone numbers, computer pass words, and other personal information. These questions are called Essential Elements of Friendly Information (EEFI). The answers to these questions are called your Critical Information List (CIL). Try to have no more than 12 items in your CIL.
Analyze Your Vulnerabilities
All of your CILs may not be vulnerable for exploitation. For example, I don’t write my passwords down, but my SSN is on my DL, even though I have the option to opt out by request (in my state). Let’s say I don’t shred my mail and I use my real name on the Internet. Are there any indicators or signatures of my operations?
Assess Risk
Not everything is at risk. We must address only those things that could affect us if compromised. This is called Risk Management vs. Risk Avoidance. A simple formula to help us with this is Threat x Vulnerability x Impact = Risk (T x V x I=R). If any one of these factors is zero, then your have no risk. Let’s say I live on a restricted high security military compound. In this situation, the threat (T) of street criminals is non-existent and is thus a “0”. Factor this in with the fact that I carry large amounts of cash and would be impacted by its loss. Use a scale of 1-5 for each element with 1 being the lowest and 5 being the highest. The carrying of cash (V) would be a 5 and the impact (I) would also be a 5. With the risk formula T x V x I=R, in this case we’d have a risk of 0 x 5 x 5=0; thus, there would be no risk. Use this formula for each of your threats and vulnerabilities to determine your unique overall risk. This also helps you to rate your risk from highest to lowest and allows you to prioritize the expenditure of your limited resources.
Apply Countermeasures
Whatever vulnerability is left after being bumped against threat and impact should be eliminated with a countermeasure. Be open minded when going through the process and try to truly take the role of the adversary.
The thing to keep in mind is that every person, group, company, or operation has a unique set of threats, EEFIs, CILs, vulnerabilities, risks, and countermeasures. There is no one size fits all.
Let’s look at an example of how this comes together for a fictitious tactical training group called the Baytown Training Group (BTG).
CRITICAL INFORMATION LIST
The CIL for BTG is:
- The names, addresses, and contact information of members
- Date time group (DTG) and specific locations of training activities
- After Action Reports (AAR) of training results that show a materiel unit weakness
- Images of members associated with BTG (Photographs may be released if member’s faces and identities are redacted and no specific mention is made of BTG. The individual member must approve the release of the redacted photograph.)
- Operation Orders (OPORD)
- Equipment load out for specific operations/missions (Generic equipment lists are releasable.)
- Communications: frequencies, call signs, cell numbers, capabilities, email addresses, and PGP encryption keys
- Supply and logistics
INDICATORS
The indicators are:
- Increased chatter on social media in the clear
- Members meeting in a public place before a training event
- Visible equipment in vehicle
- Acquisition of supplies by multiple members at the same place at the same time
- Visual compromise of operations by unauthorized personnel
- Distinctive unit insignia
THREAT
The threat is:
- Curious public
- Criminals seeking to steal weapons and equipment
- Law enforcement encumbrances
- Inadvertent disclosure or discovery during an event by unauthorized personnel
- Open source information on members and group
- Interception of communications
VULNERABILITIES
The ways that information is vulnerable for BTG:
- Open Source Intelligence (OSINT)
- Use of email between participants
- Talking in public places
- Recycle bins
- Trash
- Details on tactics, techniques, and procedures
- Social media
- Families and friends
- Interception of comms
- Visual assessment of equipment and operations
RISK
The following vulnerabilities are acceptable risks:
- Encrypted email between members containing Critical Information (CI)
- Telephone calls between members
- Conducting operations without a cover plan on secluded private property
- Use of unencrypted RF comms as long as brevity codes are used
- Use of social media as long as the forum is not available to the public and DTG and OPODR is not posted
The following vulnerabilities will be countered:
- Keep equipment covered if visible by public
- Develop a cover story if operating in public, e.g. an air soft club, geocaching, hiking group, et cetera
- Email with specific CI will be encrypted
- Brevity codes and Signal Operation Instructions will be developed when using RF comms
- Good Information Security practices will be used when handling or transporting paper media
- Practice good situational awareness and tradecraft when speaking in public
- Conduct perception management (e.g misdirection and Information Operations)
Summary
As we have learned, OPSEC is a methodological, continuous process that protects your critical information. Each person, organization, or operation will have a different CIL. OPSEC focuses on the utilization of precious time and resources to protect only that information that is critical, vulnerable, and worthwhile. Once you prioritize your information and decide what is important, it will be much easier to manage from an OPSEC perspective. OPSEC doesn’t involve protecting all information from all potential advisories.
The proper utilization of OPSEC for unique situations and day-to-day life will help create desirable outcomes, pave the way to success, and help minimize difficulties. Become familiar with the process, and get used to using it for every activity. Soon, it will become second nature, and you will have tamed the Purple Dragon!