Email a copy of 'Creating Your Own Secure Messages– Part 1, by DaytonPrepper1' to a friend
11 Comments
- Ad The Good News About Nuclear Destruction.The lethality of all nukes can be reduced by 90% when you know beforehand what to do and not do.
- Ad California Legal Rifles & Pistols!Get the firepower necessary to survive in restrictive states! WBT offers California & other state compliant rifles from any brand you want.

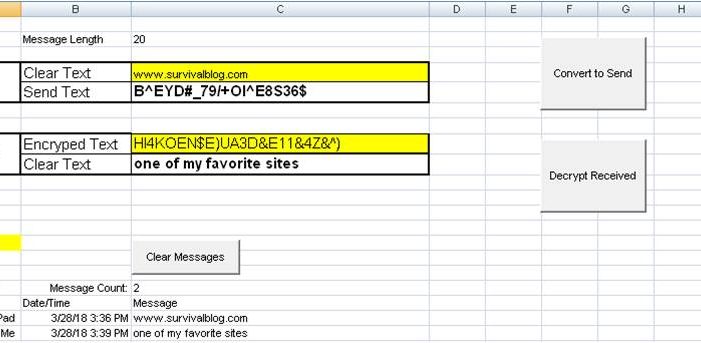
You lost any credibility you had right at the beginning when you ask the reader to use Excel (or any Microsoft product) for *anything* security related. (I’ve been a programmer & sysadmin for 30 years.)
Not all versions of excel are bait big brother versions. With 30 years experience and with software licenses already purchased, what virtual machine with team viewer can you set to share with us please? I’ll need a Vip and VPN username and password please. The concept is sound it just needs a few issues ironed out. What spreadsheet tools would you recommend instead of Excel? What OS? What kernel?
Teamviewer is a dead end in itself. Not secure at all by its design since it goes through their servers/control.
I’d use LibreOffice and some flavor of Linux. I’ll stick by my original comment: All MS software is a dealbreaker.
One of the oldest is the book method. It’s simple and ingenious, even children can use it. The drawback is similar to OTP’s. It was used during the American revolution. I hope Part 2 delves into that a little.
This is a toy, not a serious tool: never, ever roll your own encryption! Do you know where and when Excel saves backup files? Do you know if it deletes them securely, or just removes the file handle? What if it’s running with low memory and swaps to disk? What about malicious programs that can grab the Excel OLE object and read exactly what is in it? In short, this just barely works at all, and doesn’t consider even the first steps towards security. It’s irresponsible to suggest to anyone that they could use this in the wild.
ok how do I get a pad to you or somebody else that lives 500 miles away? Maybe somebody I do not know but have an urgent need to contact about dangerous information?
You can use a large book. Everyone on your list should have an exact duplicate of your book (same edition, same printing, etc.). And OPSEC rules.
This is a great article for the understanding of encryption/decryption methods. It has many uses within your teams for CW, Ameture Radio, paper messaging, etc. However, nothing is fool proof as I understand the Enigma Machine Code was broken, smoke signals from American Indians were broken, even the Uni Bomber Hideout was encoded (ratted out by his brother but it was still discovered).
The best email is protonmail – the NSA can’t break that with your keys setup properly – they are in Switzerland and will never have their servers confiscated by the government (like in the USA).
The best browser is TOR or Onion whilst utilizing VPN
The best search engine is IXQUICK – very private an no previous searches stored.
The best OS is Linix for your home computing needs.
The best cell phone is Walmart throw away phones, changing up numbers every year, and paying the monthly reload service card with cash and then using Walmart’s LAN line to call in your reloaded card numbers (not your personal phone that they can tie that to this throw away).
etc. etc. etc. Insert your own insights here….
The best vehicle is pre-2014 and not having the black box [flight recorders] in them.
It’s all about side stepping the authorities folks… nothing is foolproof.
Never ever ever ever use a computer to create a one time pad. It’s impossible to completely erase the files used during the creation process, so a hostile party with access to your hard drive will be able to break your encryption.
The other major error in this article is the use of a random number generator on a computer to create a one time pad. No matter how sophisticated such a program is, it doesn’t actually generate truly random numbers. Instead it runs a seed value through an algorithm to generate a huge list of digits that appear random to the untrained eye … but the same seed value will always generate the same string of digits. That’s easy for a hostile party to break.
To get truly random digits, toss five 10-sided dice into a Tupperware container with a clear lid, shake it, and transcribe the digits five at a time onto a single sheet of paper. Write on a hard surface, and don’t write on the top sheet of paper attached to a pad, because otherwise you might leave faint impressions behind when you remove the sheet.
Here’s a much better essay on the history, creation, and secure use of one time pads:
http://users.telenet.be/d.rijmenants/en/onetimepad.htm
What about using Apache OpenOffice (several variations)?
DaytonPrepper1, thank you for writing this article. I realize that using a computer to generate anything that you want to be secure isn’t a good idea. However, for those of us who have never used OTP encryption to compose and decode messages, your article gives us a good starting point to learn how to use this method.